Enrichment
When an entity is found in Wazuh alerts and if the settings call for the
creation of sightings and incidents, the entities specified in
enrich.types will be
created as context, if found in the alerts.
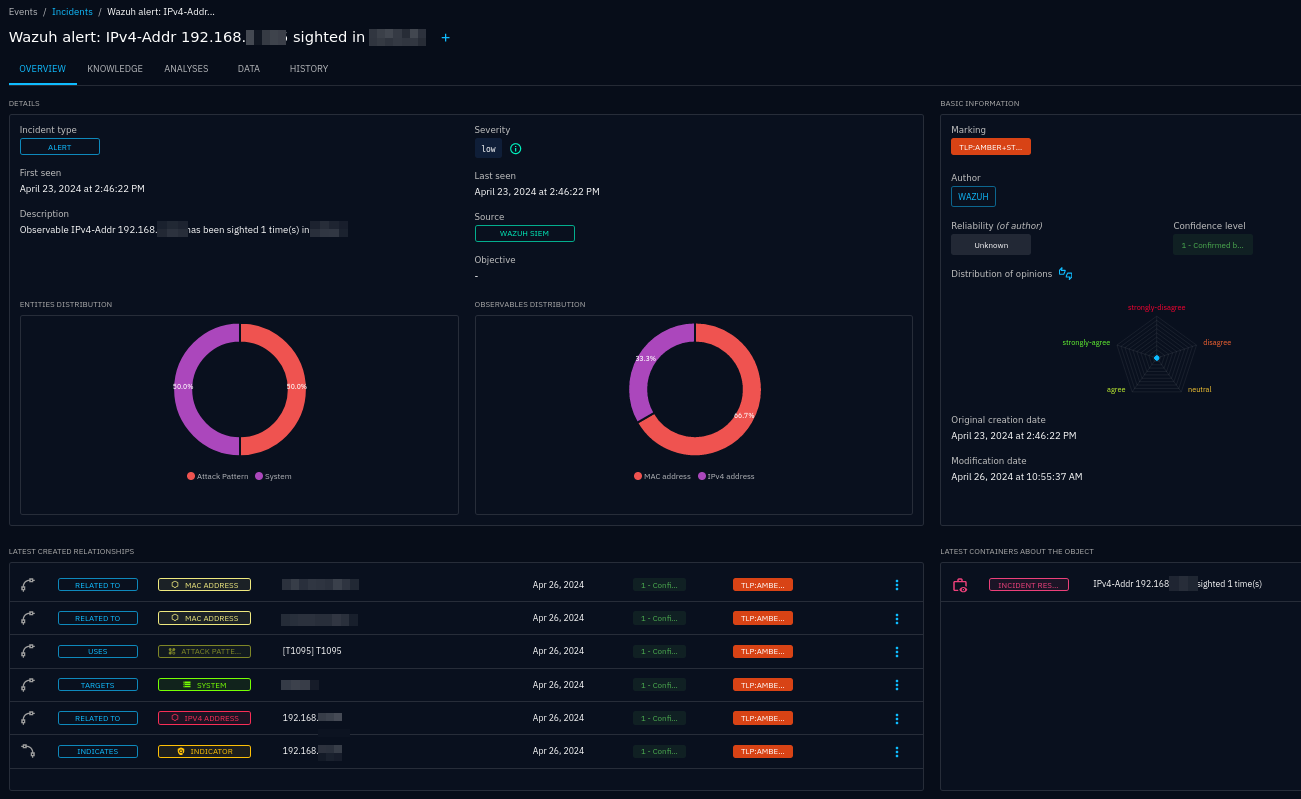
An incident created based on a sighting of an IPv4 address in a Wazuh agent (system)
Examples:
If
AttackPatternis enabled, the rule.mitre field in alerts will be used to create relationships to MITRE attack patterns. The relationship type will be uses.If
Fileis enabled, any filename / file path references will result in a File SCO being created, including an optional parent directory.If
Processis enabled, process SCOs are created from alerts like those coming from sysmon and auditd. Metadata like PID, parent processes, images as File SCOs, user accounts and command lines are extracted.
Unless specified otherwise, the relationships between the entities created and the incident are of type “related-to” (in lack of better standard-conforming types). Each relationship object contains information about which alert and which field the entity was created from. You can retrieve this information in the incident response case knowledge view by clicking on the relationship arrows.
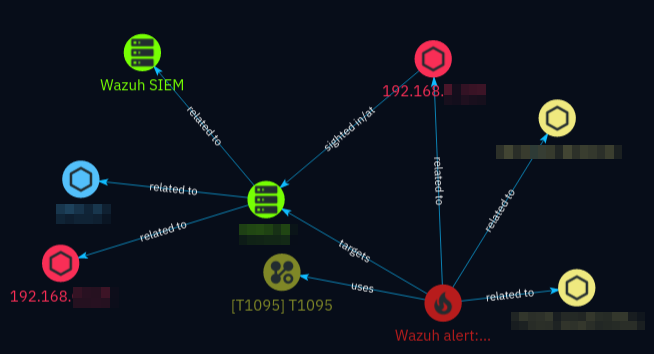
A simple incident response case with one incident and a few objects and relationships
Enriching data from alerts gives the analyst a lot more information to act on in an incident. Having to create all the individual SCOs and relationships would be incredibly time consuming.
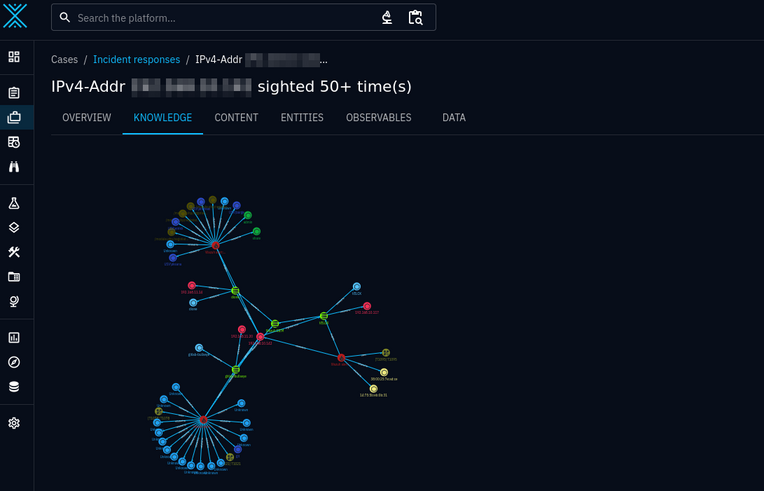
A more complicated incident response case with several incidents and many objects and relationships
See the usage section on incidents and alerting and case management for more details.
Supported entities
- class EnrichmentConfig.EntityType(value)
Entity types to enrich
See Enrichment for details.
- Account = 'user-account'
Enrich user accounts
User accounts will be created from all fields that contain usernames and/or user IDs / SIDs. The user ID may be an e-mail, for instance in alerts from Office 365 and GCP.
The following properties may be set:
account_login
user_id
- AttackPattern = 'attack-pattern'
Enrich MITRE attack patterns
Create and reference MITRE TTPs from rule.mitre.id. Only the MITRE ID is used, so unless another connector like mitre is used, the attack patterns created by opencti-wazuh will be empty, containing only the MITRE ID.
The following properties are set:
Name
External ID
- Directory = 'directory'
Enrich directories from paths
The fields used are fields known to contain only paths, without any filenames. Directory objects are still created as parent directory references whenever File objects are created. See
File.The following properties are set:
path
- Domain = 'domain-name'
Enrich domain names
Since it is often hard to distinguish hostnames from domain names, no hostname SCOs (OpenCTI’s custom SCO) are created. Hostnames may be created as domain names.
The following properties are set:
value
- EMailAddr = 'email-addr'
Enrich e-mail addresses
The following properties are set:
value
- File = 'file'
Enrich files
The following properties may be set:
name (always)
MD5
SHA1
SHA256
atime
ctime
mtime
size
- IPv4Address = 'ipv4-addr'
Enrich IPv4 addresses
The following properties are set:
value
- IPv6Address = 'ipv6-addr'
Enrich IPv6 addresses
The following properties are set:
value
- MAC = 'mac-addr'
Enrich MAC addresses
The format used is lower-case colon-delimited hexadecimal characters (EUI-48, as per the STIX standard).
The following properties are set:
value
- NetworkTraffic = 'network-traffic'
Enrich network traffic
As opposed to when searching for network traffic SCOs, enrichment will only extract network traffic from fields known to contain network traffic logs. Searching is perfomed much more broadly. Therefore, there is (currently) no support for domain names and MAC addreses as source/destination.
The following properties may be set:
src_ref (IPv4-Addr/IPv6-Addr)
dst_ref (IPv4-Addr/IPv6-Addr)
src_port
dst_port
protocols
description
At least two of src_ref, dst_ref, src_port and dst_port must be present for the SCO to be created. protocols may be inferred from the event.
Note
Unfortunately, OpenCTI has decided to focus on dst_port when displaying the network traffic SCO in graphs, or “Unknown” if the dst_port is not set. In many alerts, the destination port is not known. In order to provide a more helpful way to understand the SCO, the connector writes a connetion string in the description, like “ipv4:ssh 10.20.30.40 → 10.20.30.42:?”.
- Process = 'process'
Enrich processes
Due to a limitation set by OpenCTI (not the STIX standard), process SCOs cannot be created unless command_line can be populated (even if there is a lot of other useful information). The log will inform about this (log level info) when this happens.
sysmon
The following properties may be set (most are typically available):
pid
cwd
command_line
creator (User-Account with account_login and/or user_id)
image (File with filename (and SHA256))
parent_ref (Process with similar information about the parent process)
auditd
The following properties may be set (most are typically available):
pid
command_line
creator (User-Account with user_id (auid))
image (File with filename)
ppid (parent PID) is available, but cannot be referenced because it would imply using parent_ref and another Process object, and there is no command_line information for the parent.
- RegistryKey = 'windows-registry-key'
Enrich Windows registry keys
The following properties may be set:
key (always)
values
Note
Due to the OpenCTI bug #2574, the values are currently not imported.
- Software = 'software'
Enrich software
Currently, software SCOs are only enriched from vulnerability alerts.
The following properties may be set:
name (always)
version
- Tool = 'tool'
-
Tools are enriched by looking up names of all tools found in OpenCTI (fetched using the API when the connector starts) in fields containing command lines or names of executables. This may produce some false positives.
Note
This requires tools to exist in OpenCTI. The MITRE connector provides a number of tools, along with a number of other very useful entities.
- URL = 'url'
Enrich URLs
The following properties are set:
value
- UserAgent = 'user-agent'
Enrich user agents strings
This is a custom SCO provided by OpenCTI. Very few fields contain user agent strings. The only one so far are provided by the AWS and Office 365 integrations.
The following properties are set:
value
- Vulnerability = 'vulnerability'
Enrich vulnerabilities
Vulnerabilities are enriched from Wazuh’s vulnerability checker, from both events created when the vulnerabilities are detected, and when they are resolved.
The following properties may be set (most are typically available):
name (always)
CVSS - Score (x_opencti_cvss_base_score)
CVSS3 - Severity (x_opencti_cvss_base_severity)
CVSS3 - Attack vector (x_opencti_cvss_attack_vector)
CVSS3 - Integrity impact (x_opencti_cvss_integrity_impact)
CVSS3 - Availability impact (x_opencti_cvss_availability_impact)
CVSS3 - Confidentiality impact (x_opencti_cvss_confidentiality_impact)
Although alerts contain more metadata, there is no place to put them in the vulnerability SDO, and the connector will not override the description, since it typically contains useful information imported from another source, like MITRE.